20

300,000 login attempts and 5 observations
About a year ago, I developed a WordPress extension called WP Login Attempt Log. All it does is log every incorrect login attempt to your WordPress page and display some graphics and a way to search the logs. It logs the username, the password, the IP address and also the user agent, e.g. the browser version.
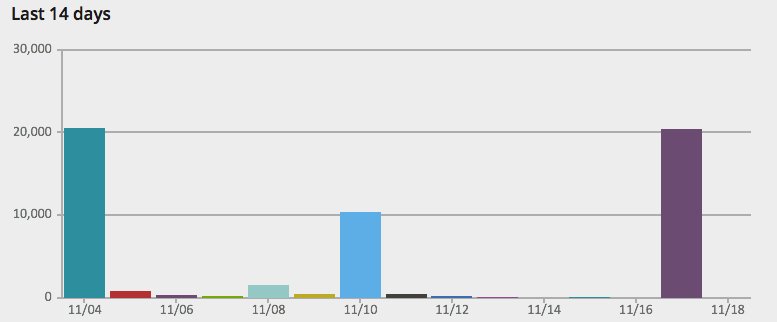
Observation number 1: attacks come and go
One thing that is striking about this graph is how much the number of attacks differ per day. Some day I will get tens of thousands of attempts, on other days I will get under 100. On average, though, I get about 2200 attempts per day, 15,000 per week and 60,000 per month. It suggests that my site is part of a rotation, or maybe that someone really wants to hack my blog on mondays.
Observation number 2: passwords are tried multiple times
All in all, there's about 36,000 unique passwords that have been used to brute-force my WordPress blog. From the total number of around 360,000 attacks, each password must is used on average of 10 times. But of course, some are used more than others, as you can see in the table below.
What's interesting is that there's not a larger amount of different passwords. From the large password database leaks the past few years – we're talking tens of millions – one could expect the amount of different passwords more closely matching the number of total attempts.
Of course, there might also just be 10 different people out to hack my blog, and they all have the same password list. :-)
Observation number 3: the most common password is "admin"
An empty password was tried around 5,300 times. Here's a list of the most used passwords, along with how many times they were used:
| Attempts | Password |
|---|---|
| 5314 | (blank) |
| 523 | admin |
| 284 | password |
| 269 | 123456 |
| 233 | admin123 |
| 230 | 12345 |
| 215 | 123123 |
| 213 | 12345678 |
| 207 | 1234 |
| 205 | admin1 |
| 203 | internet |
| 202 | pass |
| 201 | qwerty |
| 198 | mercedes |
| 194 | abc123 |
| 191 | 123456789 |
| 191 | 111111 |
| 191 | password1 |
| 190 | freedom |
| 190 | eminem |
| 190 | cheese |
| 187 | test |
| 187 | 1234567 |
| 186 | sandra |
| 184 | 123 |
| 182 | metallica |
| 181 | simonfredsted |
| 180 | friends |
| 179 | jeremy |
| 178 | 1qaz2wsx |
| 176 | administrator |
This is not a list of recommended passwords. :-) Definitely don't use any of those.
Observation number 4: 100 IP addresses account for 83% of the attempts
The top 1 IP address that have tried hacking my blog, 54.215.171.123, originates from a location you wouldn't suspect: Amazon. That IP has tried to attack my blog a whopping 45,000 times, 4 times that of the second IP on the list.
I took the top 25 offenders and did a WHOIS on them. I guess if you're looking for a server company to do your WordPress hacking, here you go:
| Attempts | IP Address | ISP | Country Code |
|---|---|---|---|
| 45465 | 54.215.171.123 | Amazon Technologies | US |
| 15287 | 63.237.52.153 | CenturyLink | US |
| 10842 | 123.30.212.140 | VDC | VN |
| 10425 | 185.4.31.190 | Green Web Samaneh Novin Co | IR |
| 10423 | 95.0.223.134 | Turk Telekom | TR |
| 10048 | 46.32.252.123 | Webfusion Internet Solutions | GB |
| 10040 | 94.23.203.18 | OVH SAS | FR |
| 10040 | 46.4.38.83 | Hetzner Online AG | DE |
| 10040 | 108.168.129.26 | iub.net | US |
| 10040 | 193.219.50.2 | Kaunas University of Technology | LT |
| 10036 | 84.95.255.154 | 012 Smile Communications | IL |
| 10035 | 80.91.189.22 | Private Joint Stock Company datagroup | UA |
| 10030 | 94.230.240.23 | Joint Stock Company TYVASVIAZINFORM | RU |
| 10030 | 123.30.187.149 | VDC | VN |
| 10029 | 89.207.106.19 | Amt Services srl | IT |
| 9328 | 67.222.98.36 | IHNetworks, LLC | US |
| 9327 | 85.95.237.218 | Inetmar internet Hizmetleri San. Tic. Ltd. Sti | TR |
| 9327 | 62.75.238.104 | PlusServer AG | DE |
| 9326 | 5.39.8.195 | OVH SAS | FR |
| 9326 | 5.135.206.157 | OVH SAS | FR |
| 9208 | 211.25.228.71 | TIME dotCom Berhad | MY |
| 9168 | 176.31.115.184 | OVH SAS | FR |
| 8804 | 78.137.113.44 | UKfastnet Ltd | GB |
| 8201 | 134.255.230.21 | INTERWERK - Rotorfly Europa GmbH & Co. KG | DE |
| 7598 | 5.199.192.70 | K Telecom | RU |
| 6952 | 85.195.91.10 | velia.net INternetdienste GmbH | DE |
| 5231 | 67.222.10.33 | PrivateSystems Networks | US |
| 3546 | 5.248.87.146 | Kyivstar PJSC | UA |
| 3202 | 78.46.11.250 | Hetzner Online AG | DE |
| 2099 | 93.45.151.167 | Fastweb | IT |
| 1940 | 92.222.16.54 | OVH SAS | FR |
Another interesting thing about this is is the amount of IPs hovering at around 10,000 attempts. It seems like there's a limit where the attacker gave up, moved on to the next target. Maybe all these are a part of a single botnet, and each machine in it is only allowed to attack 10,000 times. Who knows.
Observation number 5: protect yourself by using an unique username
WordPress hackers are really sure that you'll use a pretty standard username, or at least something to do with the name of your blog. A total of just 165 different usernames were tried, compared to the tens of thousands of passwords.
Therefore my final takeaway is to choose an obscure username as well as an obscure password. There's only 11 usernames that have been used more than a hundred times. This was kind of surprising to me.
| Attempts | Username |
|---|---|
| 164360 | admin |
| 119043 | simon |
| 15983 | administrator |
| 10787 | test |
| 10429 | adm |
| 10416 | user |
| 9871 | user2 |
| 9253 | tester |
| 8147 | support |
| 1818 | simonfredsted |
| 189 | simo |
| 57 | root |
| 57 | login |
| 56 | admin1 |
| 3 | qwerty |
| 3 | [email protected] |
| 3 | simonfredsted.com |
| 2 | aaa |
That's a lotta attacks, what do I have to fear?
WordPress blogs is one of the most targeted platforms for hackers, many sites use it, from big news organisations to small blogs like this one. If someone can get a login and start fiddling with your links, they can boost traffic to their own viagra peddling sites.
But, as long as you keep your software updated (WordPress makes this very, very easy) and keep the following two rules in mind, you're totally safe.
Bottom line: Set a lengthy password consisting of random characters, letters and digits, and use a username that's not a part of your name, site URL or "admin". Maybe just use some random letters, your password manager will remember it after all.
If you do those two things, there's nothing to worry about.
If you have your own take on this data, or think I've misinterpreted something, feel free to leave a comment below or on Hacker News – I'd love to hear your thoughts.
Nov 28, 2014 at 6:47
You could also set up fail2ban to work with wordpress to block out the bruteforce attacks. That’s what I have done with my wordpress installs
Nov 28, 2014 at 7:00
You’re storing plain text versions of passwords? What if I had a password that was genuine with one character mistake you could of probably made it out. Not good dude.
Nov 28, 2014 at 8:42
Merh,
I never enter my passwords manually, I use password managers for this. Of course, other sites and their users might have different habits – and I obviously needed to store it in plaintext to write some of this article.
Nov 28, 2014 at 7:46
Observation number 6: Don’t use WordPress. It’s possibly the most amateurish, buggy and insecure software ever created.
Nov 28, 2014 at 7:07
Any idea how they detect a successful login in WordPress? Responding with false positives for hacking attempts would render their technique almost useless or very time consuming. These fake successful login responses could then be targeted only for certain IP-addresses etc.
Nov 28, 2014 at 8:03
Priit,
I think that’s something that would make sense to add to my plugin – and your thoughts about providing false positives are spot on.
Nov 28, 2014 at 8:33
Merth: In general you’re right but it’s his own blog and the only password he might guess is his own…
After running some WP blogs for years, my simplest solution to keep 99.9% of all login attempts away is simply to limit the IP ranges that may access wp-login.php – my ISP’s range and that of my private proxy are allowed, which pretty much excludes all spammers.
Nov 28, 2014 at 9:02
How about making a an admin:admin account with no permissions that redirects to a page saying “much hacks so cyber” in a fluorescent green monospace font ;)
Nov 28, 2014 at 9:32
I don’t thing it’s quite that hard to protect against these sort of attacks as long as you keep your wordpress updated plus keep a low number of plugins because they seem to be the main source of “hacks”.
Wordpress is one of the biggest blog platforms, so, I think it’s expected to have some hacking attempts because the reward is high, don’t you agree ?
Nov 28, 2014 at 13:37
I bet you those Amazon IPs are compromised cloud instances.
Dec 7, 2014 at 12:45
[…] 300,000 WordPress hacking attempts and 5 observations […]
Dec 7, 2014 at 15:46
you can change wordpress login file name add random characters :). something like “wp-login.php” >> “wp-login_xdfsdnhfgh.php”. i have changed it on many wp site’s. even client love it. please search all wp files this list is more than year old.
wp-login.php
wp-includes/general-template.php
wp-includes/pluggable.php
wp-admin/admin-header.php
Gurjinder Singh
Dec 8, 2014 at 8:43
Also had some attacks the last days. The plugin Limit login attemps is not helping at all because the hackers are using permanently alternating IP addresses.
Btw. during the attack I was trying different Captcha-Tools. None of them was stopping the attack.
Dec 8, 2014 at 18:42
Please check out this commented code that is very strict and triggers fai2ban to ban the attacker ASAP: mainly block-bad-requests and mu-plugin
Your opinion it very welcome!
Feb 3, 2015 at 18:44
[…] 300,000 WordPress hacking attempts and 5 observations – http://simonfredsted.com/1260 […]
Apr 9, 2015 at 16:26
Thanks for the interesting observations!
And as regards hacking attempts from Amazon, it’s easily explained. There are Amazon Web Services (AWS) which are the reasons of not only hacking attempts but also excessive spider traffic.
So it may make sense to ban AWS in htaccess. Here’s the list of AWS IPs: http://researchasahobby.com/blocking-aws-scrapers/
And also, even if you have a strong password and not defauls user name, it’s not enough (although it’s already great!).
It’s not enough because of plugins and themes insecurity, or your authentication information can be stolen through insecure connections (think Wi-Fi in public places), or via trojans on your PC, vulnerabilities through your web browser etc.
Thus, apart from strong password and user name, it’s worth protecting your website more thoroughly. My receipt (a free one) is here – http://researchasahobby.com/protect-your-website-from-hacking/
Sep 21, 2016 at 18:54
Not only do I get bulk WP login attempts from OVH SAS France and OVH Hosting Montreal Canada, usually at the same time, but they also try to login to an ajax admin page, and thank goodness I don’t use Ajax.
I complained to them and never get a response and it just continues.
Sep 10, 2017 at 7:56
[…] http://simonfredsted.com/1260 […]
Mar 14, 2018 at 5:53
It’s been about two years from the original post and still, I am receiving the “Admin” failed login attempts with IPs from Amazon too. So they keep trying along the years. Of course, I receive the attempts from IPs from Ukrania, Russia, China and the like, which are no surprise to me, but it did surprise me the ones coming from Amazon and today I received login attempts from IPs from the MIT (Massachusetts Institute of Technology) and been curious about all this activity that has been going for months, I decided to search in Google about it and it took me here.
May 5, 2022 at 19:50
Multiple attempts to login to our wordpress ecommerce site today. I use https://scamalytics.com/ to trace back the i/p addresses from those attempting to login. The i/p address of the hacker is always changing to a new i/p address. I would like to know how they are able to do that so quickly as the hackers are brute forcing an attempt to break into our site every minute. I think I may have slowed things down by implementing 2 factor authorization with the WP CERBER plugin. See if that helps.